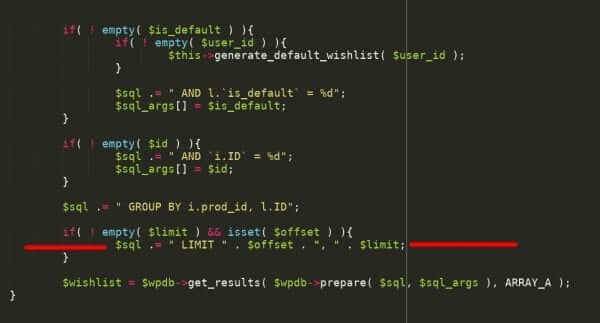
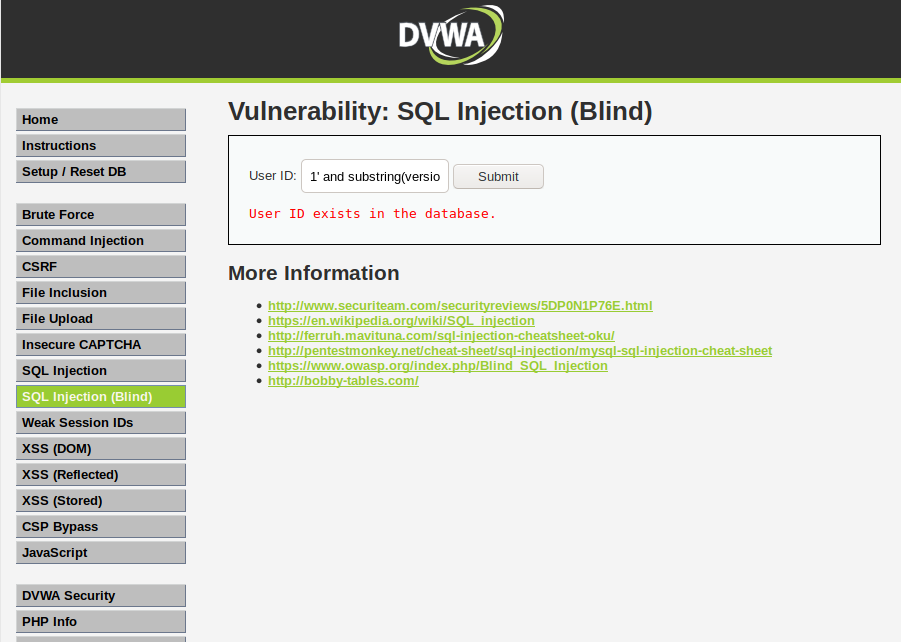
Prototype pollution: The dangerous and underrated vulnerability impacting JavaScript applications | The Daily Swig

Sumita Chakraborty on Twitter: "“I guess the reason I don't like to hear / His stories ... / Is because I'm afraid to know he was ever so vulnerable”: I love this

fuji 🌸 on Twitter: "jumping on the bandwagon to bring my ship dynamic. you'll never guess the ship https://t.co/BQ9XehoGDo" / Twitter

markstats on Twitter: "Additional graph shows how often European clubs attempt long throw-ins and the outcome (xGD10) Brentford - positive, many long throw-ins Barcelona - positive, close to zero long throw-ins Bayern -

PS4 Webkit FontFace vulnerability: Sleirsgoevy publishes new Proof Of Concept, asks for tests with firmware 9.00 - Wololo.net

New Research: Security Report Finds Ed Tech Vulnerability That Could Have Exposed Millions of Students to Hacks During Remote Learning – The 74